Carbonite Availability Powered by DoubleTake enables IT organizations to maintain the highest availability of their Windows and Linux servers by preventing downtime and data loss. The software does this using a continuous replication mechanism that maintains a secondary copy without taxing the primary system or network bandwidth. With support for physical, virtual or cloud source systems or target environments, Carbonite Availability is a comprehensive replication solution for organizations with mixed IT environments.
No delays, no data loss
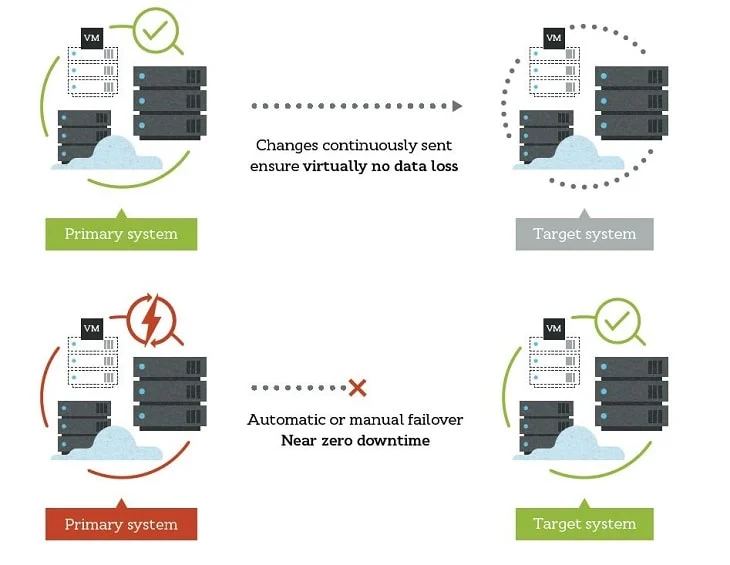
Carbonite Availability continuously replicates changes from the source environment into a secondary target anywhere in the world. Once the initial seeding is complete, changes are transmitted in real time, ensuring the replica is in sync. The software replicates files, applications or an entire server, including its system settings.
Rapid failovers prevent downtime
In the event of a disaster to one system or an entire data center, a failover to the secondary location can be easily invoked. The secondary systems spin up and users are rerouted with only a few seconds or minutes of interruption.
Negligible performance impact
The production servers protected by Carbonite Availability will not experience any performance degradation due to the replication. As changes are captured and transmitted at the byte-level, impact to network performance is minimal.
Physical systems support
Physical systems, which are typically critical to operations, are often left out of the disaster preparedness plan. To ensure all IT systems are protected, Carbonite Availability can replicate Microsoft Windows or Linux servers on any underlying platform and to any target: physical, virtual or cloud. This enables IT to unify its business continuity solution across all platforms in a single solution.
How it works
Carbonite Availability uses patented replication technology to capture changes at the byte level and replicate them between any source and target environment: physical, virtual or cloud.
First, Carbonite Availability is deployed to all the servers being protected. Through the management console, the target secondary environments are configured and replication begins with a seeding process. All data transmitted is encrypted using AES-256 encryption, and compressed using three tiers of bandwidth-saving mechanisms. Once the seeding is complete, the solution updates the target with any changes in real time.
In the event of an outage, administrators can manually or automatically fail over users to the secondary server in minutes or seconds. The recovery point can be current, or systems can be reverted to an earlier point, before an error or infection occurred.

